
Real Exam Questions and Answers as experienced in Test Center
SCS-C01 Braindumps with 100% Guaranteed Actual Questions | https:alphernet.com.au
SCS-C01 teaching - AWS Certified Security - Specialty (SCS-C01) Updated: 2024 | ||||||||||||||||||||||||||||||||||||||||||
| Pass4sure SCS-C01 real question bank | ||||||||||||||||||||||||||||||||||||||||||
 |
||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||
|
Exam Code: SCS-C01 AWS Certified Security - Specialty (SCS-C01) teaching January 2024 by Killexams.com team | ||||||||||||||||||||||||||||||||||||||||||
| AWS Certified Security - Specialty (SCS-C01) Amazon Certified teaching | ||||||||||||||||||||||||||||||||||||||||||
Other Amazon examsAWS-CSAP AWS Certified Solutions Architect - Professional (SOP-C01)AWS-CSS AWS Certified Security - Specialty ( (SCS-C01) AWS-CDBS AWS Certified Database-Specialty (DBS-C01) CLF-C01 AWS Certified Cloud Practitioner (CLF-C01) DOP-C01 AWS DevOps Engineer Professional (DOP-C01) DVA-C01 AWS Certified Developer -Associate (DVA-C01) MLS-C01 AWS Certified Machine Learning Specialty (MLS-C01) SCS-C01 AWS Certified Security - Specialty (SCS-C01) SAA-C02 AWS Certified Solutions Architect - Associate - 2023 SOA-C02 AWS Certified SysOps Administrator - Associate (SOA-C02) DAS-C01 AWS Certified Data Analytics - Specialty (DAS-C01) SAP-C01 AWS Certified Solutions Architect Professional SAA-C03 AWS Certified Solutions Architect - Associate ANS-C01 AWS Certified Advanced Networking - Specialty test (ANS-C01) SAP-C02 AWS Certified Solutions Architect - Professional PAS-C01 SAP on AWS - Specialty Certification DOP-C02 AWS Certified DevOps Engineer - Professional DVA-C02 AWS Certified Developer - Associate SCS-C02 AWS Certified Security - Specialty CLF-C02 AWS Certified Cloud Practitioner DBS-C01 AWS Certified Database - Specialty | ||||||||||||||||||||||||||||||||||||||||||
| If you are searching reliable SCS-C01 dumps on internet for free, you are wasting your time. Just buy SCS-C01 dumps consisting of real test questions in very cheap price at killexams.com, memorize, practice and relax. You need not to worry about your real SCS-C01 test. You are going to get highest marks in the SCS-C01 test. | ||||||||||||||||||||||||||||||||||||||||||
| SCS-C01 Dumps SCS-C01 Braindumps SCS-C01 Real Questions SCS-C01 Practice Test SCS-C01 dumps free Amazon SCS-C01 AWS Certified Security - Specialty (SCS-C01) http://killexams.com/pass4sure/exam-detail/SCS-C01 Question #229 A company?€™s security officer is concerned about the risk of AWS account root user logins and has assigned a security engineer to implement a notification solution for near-real-time alerts upon account root user logins. How should the security engineer meet these requirements? A. Create a cron job that runs a script to get the AWS IAM security credentials file, parse the file for account root user logins, and email the security team?€™s distribution list. B. Run AWS CloudTrail logs through Amazon CloudWatch Events to detect account root user logins and trigger an AWS Lambda function to send an Amazon SNS notification to the security team?€™s distribution list. C. Save AWS CloudTrail logs to an Amazon S3 bucket in the security team?€™s account. Process the CloudTrail logs with the security engineer?€™s logging solution for account root user logins. Send an Amazon SNS notification to the security team upon encountering the account root user login events. D. Save VPC Flow Logs to an Amazon S3 bucket in the security team?€™s account, and process the VPC Flow Logs with their logging solutions for account root user logins. Send an Amazon SNS notification to the security team upon encountering the account root user login events. Answer: B Reference: https://aws.amazon.com/blogs/mt/monitor-and-notify-on-aws-account-root-user-activity/ Question #230 A company wants to encrypt data locally while meeting regulatory requirements related to key exhaustion. The encryption key can be no more than 10 days old or encrypt more than 2^16 objects. Any encryption key must be generated on a FIPS-validated hardware security module (HSM). The company is cost-conscious, as it plans to upload an average of 100 objects to Amazon S3 each second for sustained operations across 5 data producers. Which approach MOST efficiently meets the company?€™s needs? A. Use the AWS Encryption SDK and set the maximum age to 10 days and the maximum number of messages encrypted to 2^16. Use AWS Key Management Service (AWS KMS) to generate the master key and data key. Use data key caching with the Encryption SDK during the encryption process. B. Use AWS Key Management Service (AWS KMS) to generate an AWS managed CMK. Then use Amazon S3 client-side encryption configured to automatically rotate with every object. C. Use AWS CloudHSM to generate the master key and data keys. Then use Boto 3 and Python to locally encrypt data before uploading the object. Rotate the data key every 10 days or after 2^16 objects have been uploaded to Amazon S3. D. Use server-side encryption with Amazon S3 managed encryption keys (SSE-S3) and set the master key to automatically rotate. Answer: C Question #231 A company is setting up products to deploy in AWS Service Catalog. Management is concerned that when users launch products, elevated IAM privileges will be required to create resources. How should the company mitigate this concern? A. Add a template constraint to each product in the portfolio. B. Add a launch constraint to each product in the portfolio. C. Define resource update constraints for each product in the portfolio. D. Update the AWS CloudFormation template backing the product to include a service role configuration. Answer: B Reference: https://aws.amazon.com/blogs/mt/how-to-launch-secure-and-governed-aws-resources-with-aws-cloudformation-and-aws-service-catalog/ Question #232 A company is implementing a new application in a new AWS account. A VPC and subnets have been created for the application. The application has been peered to an existing VPC in another account in the same AWS Region for database access. Amazon EC2 instances will regularly be created and terminated in the application VPC, but only some of them will need access to the databases in the peered VPC over TCP port 1521. A security engineer must ensure that only the EC2 instances than need access to the databases can access them through the network. How can the security engineer implement this solution? A. Create a new security group in the database VPC and create an inbound rule that allows all traffic from the IP address range of the application VPC. Add a new network ACL rule on the database subnets. Configure the rule to TCP port 1521 from the IP address range of the application VPC. Attach the new security group to the database instances that the application instances need to access. B. Create a new security group in the application VPC with an inbound rule that allows the IP address range of the database VPC over TCP port 1521. Create a new security group in the database VPC with an inbound rule that allows the IP address range of the application VPC over port 1521. Attach the new security group to the database instances and the application instances that need database access. C. Create a new security group in the application VPC with no inbound rules. Create a new security group in the database VPC with an inbound rule that allows TCP port 1521 from the new application security group in the application VPC. Attach the application security group to the application instances that need database access, and attach the database security group to the database instances. D. Create a new security group in the application VPC with an inbound rule that allows the IP address range of the database VPC over TCP port 1521. Add a new network ACL rule on the database subnets. Configure the rule to allow all traffic from the IP address range of the application VPC. Attach the new security group to the application instances that need database access. Answer: A Question #233 A company is running an application on Amazon EC2 instances in an Auto Scaling group. The application stores logs locally. A security engineer noticed that logs were lost after a scale-in event. The security engineer needs to recommend a solution to ensure the durability and availability of log data. All logs must be kept for a minimum of 1 year for auditing purposes. What should the security engineer recommend? A. Within the Auto Scaling lifecycle, add a hook to create an attach an Amazon Elastic Block Store (Amazon EBS) log volume each time an EC2 instance is created. When the instance is terminated, the EBS volume can be reattached to another instance for log review. B. Create an Amazon Elastic File System (Amazon EFS) file system and add a command in the user data section of the Auto Scaling launch template to mount the EFS file system during EC2 instance creation. Configure a process on the instance to copy the logs once a day from an instance Amazon Elastic Block Store (Amazon EBS) volume to a directory in the EFS file system. C. Build the Amazon CloudWatch agent into the AMI used in the Auto Scaling group. Configure the CloudWatch agent to send the logs to Amazon CloudWatch Logs for review. D. Within the Auto Scaling lifecycle, add a lifecycle hook at the terminating state transition and alert the engineering team by using a lifecycle notification to Amazon Simple Notification Service (Amazon SNS). Configure the hook to remain in the Terminating:Wait state for 1 hour to allow manual review of the security logs prior to instance termination. Answer: A Question #234 A company needs to retain log data archives for several years to be compliant with regulations. The log data is no longer used, but it must be retained. What is the MOST secure and cost-effective solution to meet these requirements? A. Archive the data to Amazon S3 and apply a restrictive bucket policy to deny the s3:DeleteObject API. B. Archive the data to Amazon S3 Glacier and apply a Vault Lock policy. C. Archive the data to Amazon S3 and replicated it to a second bucket in a second AWS Region. Choose the S3 Standard-Infrequent Access (S3 Standard-IA) storage class and apply a restrictive bucket policy to deny the s3:DeleteObject API. D. Migrate the log data to a 16 TB Amazon Elastic Block Store (Amazon EBS) volume. Create a snapshot of the EBS volume. Answer: C Question #235 A company uses an Amazon S3 bucket to store reports. Management has mandated that all new objects stored in this bucket must be encrypted at rest using server-side encryption with a client specified AWS Key Management Service (AWS KMS) CMK owned by the same account as the S3 bucket. The AWS account number is 111122223333, and the bucket name is reportbucket. The company?€™s security specialist must write the S3 bucket policy to ensure the mandate can be implemented. Which statement should the security specialist include in the policy? A. B. C. D. Answer: A Question #236 A company website runs on Amazon EC2 instances behind an Application Load Balancer (ALB). The instances run in an Auto Scaling group across multiple Availability Zones. There is an Amazon CloudFront distribution in front of the ALB. Users are reporting performance problems. A security engineer discovers that the website is receiving a high rate of unwanted requests to the CloudFront distribution originating from a series of source IP addresses. How should the security engineer address this problem? A. Using AWS Shield, configure a deny rule with an IP match condition containing the source IPs of the unwanted requests. B. Using Auto Scaling, configure the maximum an instance value to an increased count that will absorb the unwanted requests. C. Using an Amazon VPC NACL, configure an inbound deny rule for each source IP CIDR address of the unwanted requests. D. Using AWS WAF, configure a web ACL rate-based rule on the CloudFront distribution with a rate limit below that of the unwanted requests. Answer: D Question #237 A developer is building a serverless application hosted on AWS that uses Amazon Redshift as a data store. The application has separate module for read/write and read-only functionality. The modules need their own database users for compliance reasons. Which combination of steps should a security engineer implement to grant appropriate access? (Choose two.) A. Configure cluster security groups for each application module to control access to database users that are required for read-only and read-write. B. Configure a VPC endpoint for Amazon Redshift. Configure an endpoint policy that maps database users to each application module, and allow access to the tables that are required for read-only and read/write. C. Configure an IAM policy for each module. Specify the ARN of an Amazon Redshift database user that allows the GetClusterCredentials API call. D. Create local database users for each module. E. Configure an IAM policy for each module. Specify the ARN of an IAM user that allows the GetClusterCredentials API call. Answer: AD Question #238 A company uses an external identity provider to allow federation into different AWS accounts. A security engineer for the company needs to identify the federated user that terminated a production Amazon EC2 instance a week ago. What is the FASTEST way for the security engineer to identify the federated user? A. Review the AWS CloudTrail event history logs in an Amazon S3 bucket and look for the TerminateInstances event to identify the federated user from the role session name. B. Filter the AWS CloudTrail event history for the TerminateInstances event and identify the assumed IAM role. Review the AssumeRoleWithSAML event call in CloudTrail to identify the corresponding username. C. Search the AWS CloudTrail logs for the TerminateInstances event and note the event time. Review the IAM Access Advisor tab for all federated roles. The last accessed time should match the time when the instance was terminated. D. Use Amazon Athena to run a SQL query on the AWS CloudTrail logs stored in an Amazon S3 bucket and filter on the TerminateInstances event. Identify the corresponding role and run another query to filter the AssumeRoleWithWebIdentity event for the user name. Answer: A Reference: https://aws.amazon.com/blogs/security/how-to-easily-identify-your-federated-users-by-using-aws-cloudtrail/ Question #239 A company has two software development teams that are creating applications that store sensitive data in Amazon S3. Each team?€™s data must always be separate. The company?€™s security team must design a data encryption strategy for both teams that provides the ability to audit key usage. The solution must also minimize operational overhead. What should the security team recommend? A. Tell the application teams to use two different S3 buckets with separate AWS Key Management Service (AWS KMS) AWS managed CMKs. Limit the key policies to allow encryption and decryption of the CMKs to their respective teams only. Force the teams to use encryption context to encrypt and decrypt. B. Tell the application teams to use two different S3 buckets with a single AWS Key Management Service (AWS KMS) AWS managed CMK. Limit the key policy to allow encryption and decryption of the CMK only. Do not allow the teams to use encryption context to encrypt and decrypt. C. Tell the application teams to use two different S3 buckets with separate AWS Key Management Service (AWS KMS) customer managed CMKs. Limit the key policies to allow encryption and decryption of the CMKs to their respective teams only. Force the teams to use encryption context to encrypt and decrypt. D. Tell the application teams to use two different S3 buckets with a single AWS Key Management Service (AWS KMS) customer managed CMK. Limit the key policy to allow encryption and decryption of the CMK only. Do not allow the teams to use encryption context to encrypt and decrypt. Answer: B Question #240 A security engineer is designing a solution that will provide end-to-end encryption between clients and Docker containers running in Amazon Elastic Container Service (Amazon ECS). This solution will also handle volatile traffic patterns. Which solution would have the MOST scalability and LOWEST latency? A. Configure a Network Load Balancer to terminate the TLS traffic and then re-encrypt the traffic to the containers. B. Configure an Application Load Balancer to terminate the TLS traffic and then re-encrypt the traffic to the containers. C. Configure a Network Load Balancer with a TCP listener to pass through TLS traffic to the containers. D. Configure Amazon Route to use multivalue answer routing to send traffic to the containers. Answer: B Question #241 A company uses an AWS Key Management Service (AWS KMS) CMK to encrypt application data before it is stored. The company?€™s security policy was recently modified to require encryption key rotation annually. A security engineer must ensure that annual global key rotation is enabled for the key without making changes to the application. What should the security engineer do to accomplish this requirement? A. Create new AWS managed keys. Configure the key schedule for the annual rotation. Create an alias to point to the new keys. B. Enable automatic annual key rotation for the existing customer managed CMKs. Update the application encryption library to use a new key ID for all encryption operations. Fall back to the old key ID to decrypt data that was encrypted with previous versions of the key. C. Create new AWS managed CMKs. Configure the key schedule for annual rotation. Create an alias to point to the new CMKs. D. Enable automatic annual key rotation for the existing customer managed CMKs. Update the application encryption library to use a new key ID for all encryption operations. Create a key grant for the old CMKs and update the code to point to the ARN of the grants. Answer: D Reference: https://docs.aws.amazon.com/kms/latest/developerguide/rotate-keys.html Question #242 A company is collecting AWS CloudTrail log data from multiple AWS accounts by managing individual trails in each account and forwarding log data to a centralized Amazon S3 bucket residing in a log archive account. After CloudTrail introduced support for AWS Organizations trails, the company decided to further centralize management and automate deployment of the CloudTrail logging capability across all of its AWS accounts. The company?€™s security engineer created an AWS Organizations trail in the master account, enabled server-side encryption with AWS KMS managed keys (SSE- KMS) for the log files, and specified the same bucket as the storage location. However, the engineer noticed that logs recorded by the new trail were not delivered to the bucket. Which factors could cause this issue? (Choose two.) A. The CMK key policy does not allow CloudTrail to make encrypt and decrypt API calls against the key. B. The CMK key policy does not allow CloudTrail to make GenerateDatakey API calls against the key. C. The IAM role used by the CloudTrail trail does not have permissions to make PutObject API calls against a folder created for the Organizations trail. D. The S3 bucket policy does not allow CloudTrail to make PutObject API calls against a folder created for the Organizations trail. E. The CMK key policy does not allow the IAM role used by the CloudTrail trail to use the key for cryptographical operations. Answer: AD Question #243 A company?€™s AWS CloudTrail logs are all centrally stored in an Amazon S3 bucket. The security team controls the company?€™s AWS account. The security team must prevent unauthorized access and tampering of the CloudTrail logs. Which combination of steps should the security team take? (Choose three.) A. Configure server-side encryption with AWS KMS managed encryption keys (SSE-KMS) B. Compress log file with secure gzip. C. Create an Amazon EventBridge (Amazon CloudWatch Events) rule to notify the security team of any modifications on CloudTrail log files. D. Implement least privilege access to the S3 bucket by configuring a bucket policy. E. Configure CloudTrail log file integrity validation. F. Configure Access Analyzer for S3. Answer: BCE For More exams visit https://killexams.com/vendors-exam-list Kill your test at First Attempt....Guaranteed! | ||||||||||||||||||||||||||||||||||||||||||
Sustainability initiatives have been organised for most of the agricultural commodities of the Pan Amazon, including palm oil, soy and beef, but also for coffee and cacao. Several of these initiatives have adopted the term roundtable in their names because it conveys the notion of inclusiveness that is a core concept in these multi-stakeholder initiatives. Typically, the stakeholders include all the participants in a supply chain, from the farmer to the retailer, but also commodity traders, consumer goods manufacturers, banks and service supplies, as well as civil society groups. Their shared goal is to identify effective solutions to the social and environmental challenges associated with conventional production systems. The mechanism used to reform supply chains is typically a voluntary certification system that verifies that the production, trade and transformation of a commodity has complied with a set of best practices that have been agreed to by all the parties. The search for consensus is important, because it means all of the stakeholders have agreed to accept this package of solutions and commit to supporting the commercialisation of the goods that have been certified as sustainable. Some environmental activists view these initiatives as a form of greenwash and have questioned their efficacy. Participating companies certify the production within their own supply chain, but roundtable initiatives have not succeeded in transforming their respective sectors. Demand for certified commodities has failed to attract a critical mass of producers that would actually transform the market and change the economic drivers of deforestation. Adoption is highest for coffee (40%) and cocoa (22%), while commodities linked to industrial plantations tend to be lower: palm oil (20%), sugar (3%) soy (2%) and beef (<1%). Part of the explanation for the slow uptake of the voluntary standards is the lack of demand; typically, only about fifty per cent of certified production is actually sold as a certified commodity. 
The lack of uptake is yet another manifestation of the dilemma of allocating the cost of environmental protection and social justice. Sustainability protocols cost money, which either adds to the price of a consumer good or reduces the profit margin of commodity producers. Although North American and European consumers are concerned about deforestation, most still choose a lower-cost product, while those in Asia, Latin America and the Middle East are overwhelmingly focused on price. Moreover, global commodity markets are dominated by producers on landscapes that were transformed by agriculture decades or centuries in the past, and these farmers operate without fear of being accused of environmental crimes. Consequently, traders are not motivated to pay a premium to farmers on the agricultural frontier. A few producers seek to differentiate their products as organic, deforestation-free, fair-trade or antibiotic-free because they are selling their products into a differentiated market and receive a premium for their production in compensation for the extra cost and reduced yields that these systems [allegedly] entail. Others participate because it guarantees them market access. Most producers opt to circumvent the voluntary guidelines or sell to traders unconcerned about sustainability or just ignore the whole process entirely. Social advocates have questioned the economic benefits of certification because they tend to discriminate against small-scale producers who cannot meet the record-keeping and logistical demands of a certification process. These protocols are negotiated by large-scale producers that dominate the roundtable initiatives and tailor the certification criteria to their supply chains. As formalisation spreads throughout national and international markets, smallholders could be increasingly marginalised within regional and even local markets in contradiction with the stated social objectives of these certification schemes. “A Perfect Storm in the Amazon” is a book by Timothy Killeen and contains the author’s viewpoints and analysis. The second edition was published by The White Horse in 2021, under the terms of a Creative Commons license (CC BY 4.0 license). Read the other excerpted portions of chapter 3 here:
Chapter 3. Agriculture: Profitability determines land use
 Amazon: Ranking the Magnificent 7 for 2024, Blue Harbinger Daria Nipot 2023 was largely a tale of two markets. The “S&P 493” (roughly two-thirds of the index, by market cap) was up 20.3% (on average), while the seven largest mega-cap stocks (i.e. "The Magnificent 7”) were up ~100%, on average (see table below). In this report, they rank each of the Magnificent 7 stocks for 2024, with a special focus on Amazon (NASDAQ:AMZN) (including an update on its business, its four big growth opportunities, valuation and risks). They conclude with their stern opinion on investing in Amazon (and the Magnificent 7) in 2024, especially as compared to non-mega-cap growth stock opportunities. The Magnificent 7For some perspective, here is a look at the performance of the Magnificent 7 for 2023 (they are ranked by market cap in the table). They all dramatically outperformed the S&P 500 for the year, but this comes after a weak 2022 (see the 2-year total returns column). 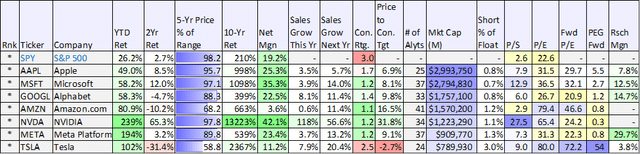
data as of 12/31/2023 (StockRover) (AAPL) (MSFT) (GOOGL) (GOOG) (NVDA) (META) (TSLA) You’ll also notice in the table above that Wall Street’s consensus rating for all of these stocks is significantly better than the S&P 500 (note: a 1.0 rating is a “strong buy” whereas a 5.0 rating is a “strong sell”). Also worth mentioning, you can see how they compare on various valuation metrics, such as price-to-earnings and price-to-sales, but there is always more to the story than just those numbers (more on this later). Also, for a little more perspective, here is a look at just how lopsided performance was in 2023 (i.e. an unusually large percentage of individual stocks (72%) underperformed the S&P 500 because the gains were dominated by the “magnificent 7” representing ~one-third of the total market cap). 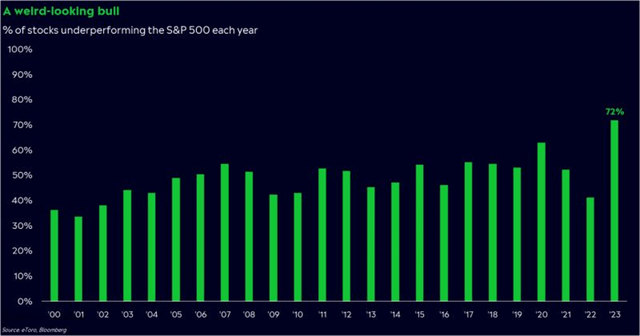
eToro, Bloomberg Next, we’ll take a closer look at one of the magnificent 7 stocks in particular, Amazon. AmazonMany people think of Amazon as the website where you search for whatever you want, click “buy,” and then it shows up at your home or office some days later. And while that part of its business generates the majority of its revenues (84%), basically all of the profits come from its cloud-data hosting service (Amazon Web Services, AWS), which makes up only 16% of the revenues. 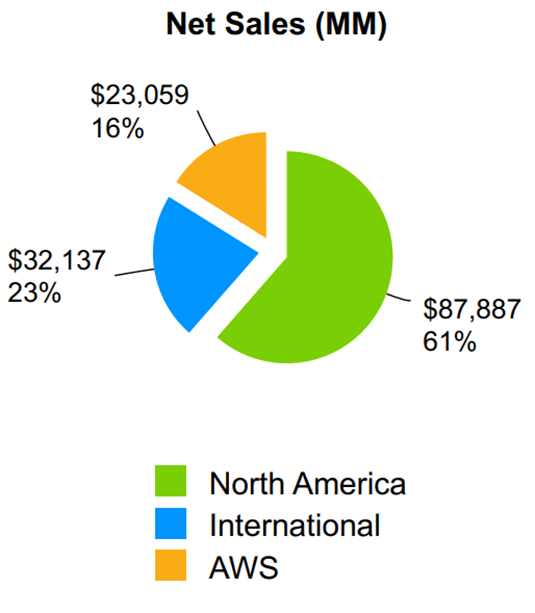 Amazon Q3 Investor Presentation So with that high-level backdrop in mind, let’s get into the four big factors that they see driving growth for Amazon in 2024 and beyond. 1. Amazon Web Service (“AWS”), Despite CompetitionAmazon Web Service is the leader in the cloud market because Amazon had the foresight to recognize the massive secular opportunities ahead of the traditional big boys, like Microsoft, Google and others (and because Amazon had an infrastructure head start via its online marketplace). You can see the recent worldwide cloud market share in the following graphic. 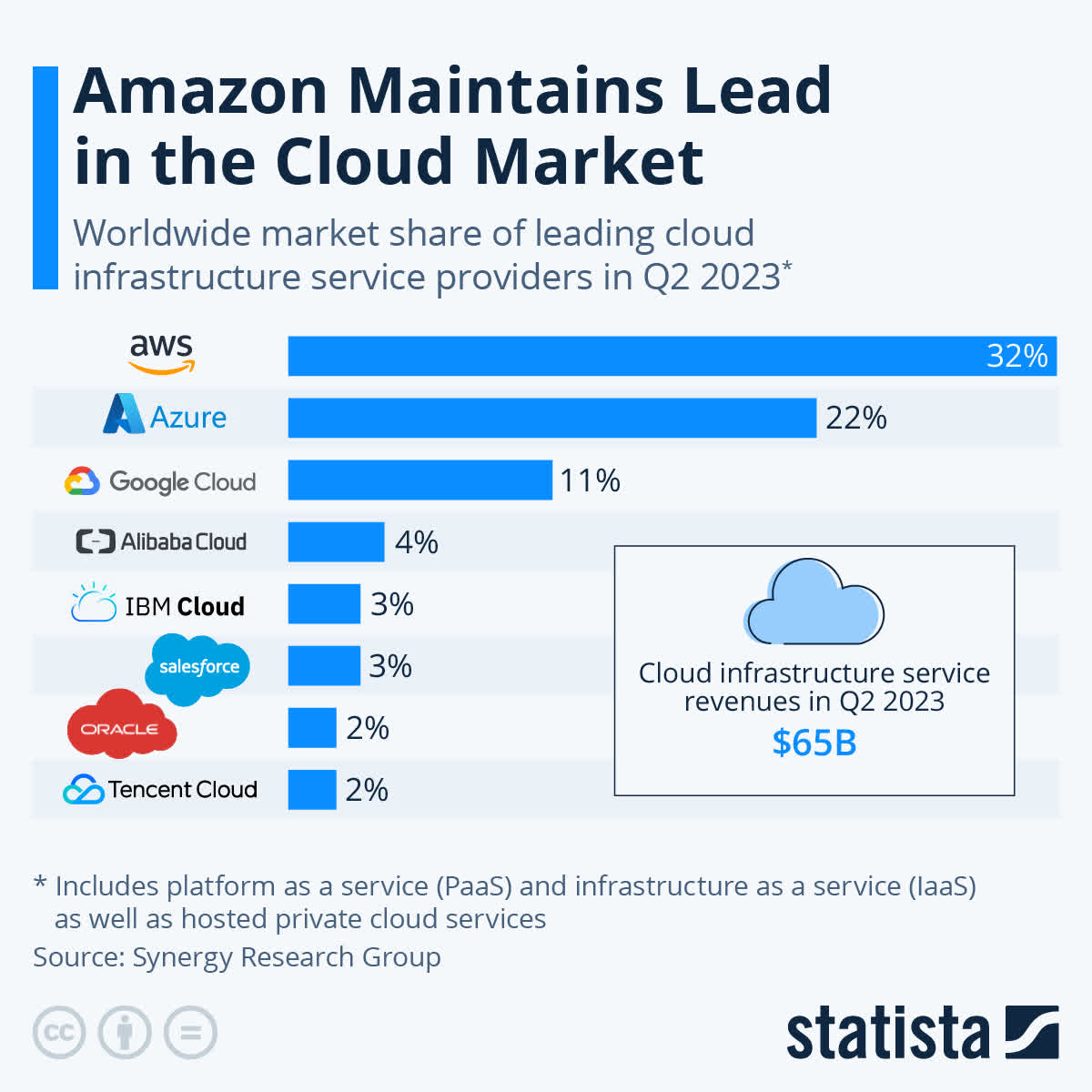 Statista (BABA) (IBM) (CRM) (ORCL) (OTCPK:TCEHY) However, Microsoft and Google have been gaining on Amazon in this space. For example, according to estimates from Synergy Research Group:
Cloud competition is absolutely a concern for Amazon, but it is important to keep it in perspective. Specifically, Amazon is still the worldwide cloud leader, it is very profitable in this space, and it is still growing rapidly. Moreover, the cloud opportunity (and the digitization of everything) remains perhaps the biggest technology secular trend in the world, expected to continue growing rapidly for many years, and recently being accelerated by Artificial Intelligence (more on Amazon AI later). 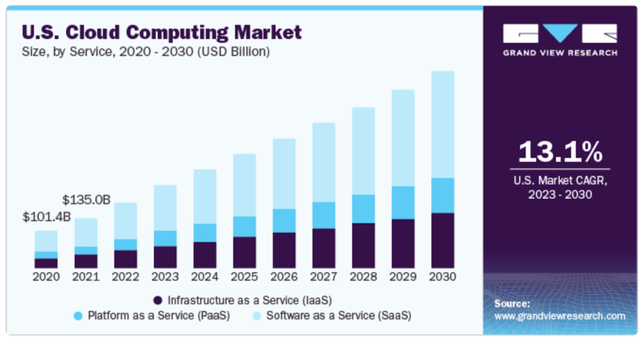
Grandview Research 2. Ads Are Coming to Prime VideoThe next big theme that will impact Amazon’s business in 2024 and beyond is the addition of advertising to Amazon Prime videos (expected to begin near the end of January). Amazon Prime is a subscription service that gives users access to additional services (including faster delivery, streaming music and videos, and more). According to this article, customers will be able to pay an additional $2.99 per month to avoid ads (a prime membership costs $14.99 per month or only $139 if you pay annually). According to the company
Considering the large size of Amazon Prime (over 200 million customers worldwide), ads have the potential to meaningfully move the revenue needle for the company. 3. Artificial Intelligence Is HereWith technological advances in artificial intelligence, it has become a major theme (and growth driver) across businesses in every sector. And Amazon is also looking to capitalize on AI opportunities. According to the company:
Given the profound impact AI is expected to have on the economy, it’s important that Amazon stays at least on pace with the curve so as to not be left behind (as many slower movers inevitably will be). The company says it is also using AI beyond AWS, including helping customers better discover products that meet their needs, forecasting inventory levels, and improving delivery, to name a few. 4. The Andy Jassy FactorAndy Jassy joined Amazon in 1997, he founded AWS, and he became CEO (succeeding Jeff Bezos) in 2021. Bezos wisely left near the peak of the pandemic bubble (he went out on top), and Jassy has been at the helm while the market bubble burst, and they believe he now has something to prove. Specifically, Jassy is a winner (he went to Harvard and founded the largest cloud service in the world, AWS), but his compensation has been terrible because it has been tied to the stock price (which has not been great during his short-term as CEO so far). For example, Jassy’s pay was just $1.3 million in 2022 (tiny for a mega-cap CEO) because, again, it is tied mainly to stock performance (which was terrible in 2022). Jassy’s compensation will likely be much bigger for 2023 (Amazon shares were up 80%), but they suspect he still has a lot more to prove. They like Jassy as CEO and suspect he will do big things with success in the years ahead (such as growing AWS, succeeding with advertising initiatives and prudently implementing AI initiatives). Amazon’s ValuationAs you can see in their earlier table, Amazon has the second lowest forward PEG ratio (i.e. Price/Earnings/Growth (lower is better)) among the Magnificent 7 (second only to Tesla, which they view as a much more volatile and risky business). Also, don’t be misled by Amazon’s low price-to-sales ratio (it's attractive, but not as attractive as it may seem considering the low margins on the Amazon online marketplace business). However, the forward revenue growth rate is strong, Wall Street rates the shares very highly versus mega-cap peers and (unlike most other mega-caps) Amazon shares are still well below their all-time high. In their view, Amazon is a healthy growing business, benefiting from large secular trends and with a highly competent CEO at the helm. Amazon’s RisksLike any company, Amazon faces a variety of risks. For example, the introduction of ads on Prime could backfire. The company may lose customers over it if not done correctly (especially considering there are a variety of streaming competitors). Initially, the magic of streaming was that there were no ads, but as that now changes and competition has increased, Amazon Prime Ads may not be a slam dunk. Another risk is that Microsoft Azure and Google Cloud are both growing faster than AWS. Fortunately, the cloud is a very big place (and is expected to keep growing rapidly for many years, see their earlier chart from Grandview Research) so there is room for multiple big winners. Nonetheless, AWS competition is a risk. Another risk is share price volatility. Recall these shares were down dramatically in 2022, up dramatically in 2023, and they could again be volatile in 2024. So with that information on Amazon, let’s briefly consider the other Magnificent 7 stocks, before drawing a few final conclusions. The Other Magnificent 7 Stocks:
Ranking The Magnificent 7:We wouldn’t bet against the Magnificent 7 in 2024, but they do believe some may perform meaningfully better than others, and that investors may want to reconsider the size of their allocations to these stocks in their portfolios. For 2024, we’re breaking the Magnificent 7 into three tiers: Tier 3: If the market’s aggregate taste shifts from growth to value in 2024, Apple may be the winner. It is arguably one of the steadiest Magnificent 7 stocks (people aren’t going to get rid of their iPhones, even if the market crashes). But Apple has the lowest expected growth rate and trades at a fairly rich forward PEG ratio. The business is still better than most companies in the world, just not necessarily better than the other Magnificent 7 stocks, in their opinion. Tier 2: We’re putting Tesla in this group as the valuation has gotten stretched, and Elon will need to pull another rabbit out of his hat (in an election year, no less, when he’ll inevitably be putting out fires at Twitter (now “X”)). They could end up being very wrong on this one, but Tesla is Tier 2 here. Tier 1: They like Amazon, Alphabet, Microsoft, Meta and Nvidia, but the question is how much of them you want to hold. They make up a truly enormous percentage of the U.S. (and global) market cap, and it could be quite risky to avoid them altogether. However, considering the tremendously strong performance in 2023, you may or may not want to be “overweight” these names for 2024. For a little more perspective, they offer a few non-mega-cap growth stock alternatives and ideas below. Non-Mega-Cap Growth AlternativesWe noted above how the Magnificent 7 dominated the markets in 2023, but if you actually look closer, there were plenty of non-mega-cap growth stocks that also performed extremely well (in most cases, rebounded very hard), and may be poised for strong gains again in 2024. For example, check out the following table which includes top-performing non-mega-cap growth stocks in 2023, that are also rated very highly by Wall Street. In fact, many of them have dramatically more price appreciation potential than the Magnificent 7, as per Wall Street analysts, as you can see in the following table. 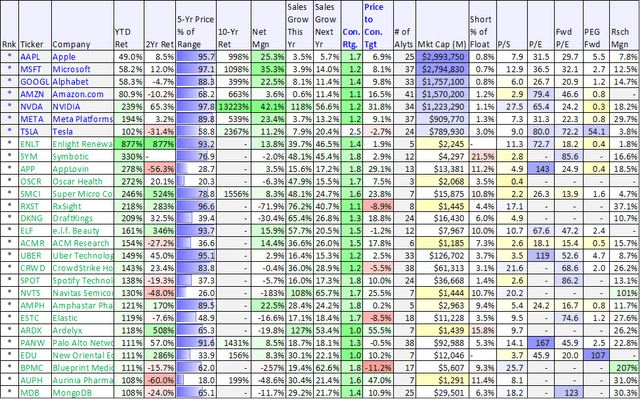
data as of 12/31/2023 (StockRover) (SMCI) (CRWD) (UBER) (PANW) (MDB) Also, here are the same data points for highly rated non-mega-cap growth stocks that underperformed the market in 2023. These names have a ton of upside potential in 2024, as per Wall Street, as you can see in the table below. 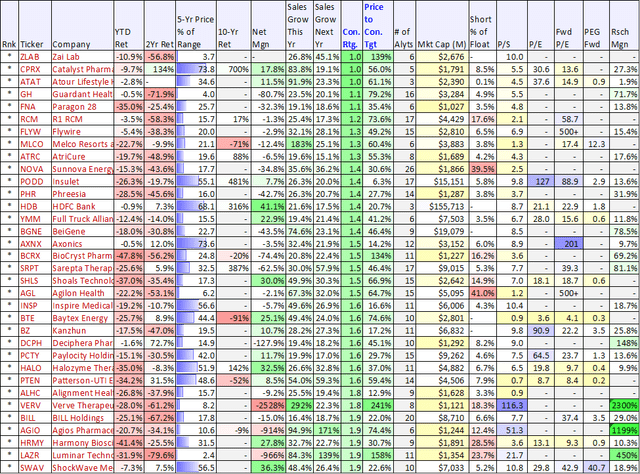
data as of 12/31/2023 (StockRover) If you are looking to diversify away some of your exposure to the Magnificent 7 (especially after the incredible 2023 performance), you might find a few worthwhile ideas in the data above. ConclusionDespite the strong 2023 performance, Amazon (and the Magnificent 7, in general) remain extremely attractive businesses. Amazon in particular, is the only Magnificent 7 stock that still sits well below its all-time high (other than Tesla, which they view as a wildcard, especially considering the distractions CEO Elon Musk increasingly faces). And despite Amazon’s incomplete price rebound (so far), it has some extremely attractive qualities, such as AWS, the launch of advertising, AI, current valuation, and CEO Andy Jassy. Some investors believe the market’s infatuation with “The Magnificent 7” has gone too far, and now prefer to focus on smaller, lessor known, growth stocks with potentially much more upside (such as those they shared in the tables in this report). However, considering the Magnificent 7 makes up such a large (and important) part of the global market cap, we’re absolutely not willing to completely sell out of them altogether. Regarding Amazon, we’re currently long-shares (in their Disciplined Growth Portfolio) and have no intention of selling anytime soon. How much did the Arcteryx stock value go up over December? Christmas may be over but now it’s time to show off everything you got for Christmas to your housemates. Whether it was on your list to Santa (sending your mum an Amazon link) or you were suggesting not-so-subtle Secret Santa hints to your housemates, here’s 8 Christmas presents which mean you’re certified Fallow-coded. 1. Anything ArcteryxWhether it’s a beanie or jacket, this brand simply has to be part of your fit come Semester 2. At risk of looking like a substitute geography teacher, these will match your Salomon trainers perfectly. It’s built to survive the slopes, but will it survive the 142?
2. Some decksEvery single boy in Fallowfield seems to be a maestro on the decks, promising the best mix of deep house funk techno you’ve ever heard at pres. These boys will be headlining XLR in no time.
3. A Crystal Bar Selection BoxForget Cadbury’s and Mars, who wants to open up the same old selection box with a Chomp that no one wants. This is sure to satisfy everyone’s tastes, as long as they don’t include Lemon and Lime!
4. A Multi-pack of Pot NoodleLet’s face it, after a month of home cooking, no ones in the mood to start cooking chicken rice and broccoli every night just yet. These will sort you out for the moment, especially when you’ve not got much time before the first 256 Tuesday back. 5. A 16 pack of MonsterExam season is looming a lot sooner than we’d like after New Year. Might as well get stocked up early ready for some mammoth revision sessions and test all-nighters in Blue 2. White Monster for me please.
6. A Chester’s Chicken Gift CardSome people want to get loaded up with Costa or Pret credit, but not a Fallowfield boy. This will make those end of night fried chicken cravings a lot easier to cave to. It might even last beyond re-freshers week. Bonus points if a Chester’s Hoodie was also under the tree. 7. A date from HingeWe’re getting a bit less realistic now, but after 68 failed pick-up lines on Hinge in Semester 1, Santa might just be able to share a bit of Christmas magic with you to get your dating life back on track.
8. 256 Tuesday Black CardAnd finally every single Fallowfield boy’s dream. These don’t even exist but that doesn’t stop you dreaming about one. Guaranteed access to Fallowfield’s biggest night, queue jump and all. There are some things that just sound too good to be true, but this is what Christmas miracles are for. Whether you're famous for your homemade holiday cookies or just want a festive place to store Santa's chocolate chips, this ceramic jar is a must. Standing nearly a foot tall, it's hand-painted and made from sturdy earthenware, ensuring it'll last decades. Plus, at $45, it's currently nearly half off the list price of $78. Amazon is practically giving these favorites awayA new year is here, and with it, a chance to create new habits, try new hobbies, restock or redecorate your home and tackle other projects. And thanks to Amazon’s New Year’s sale, you can do it all at great prices. The sale is huge — tons of products are discounted sitewide, including popular favorites and bestsellers for up to 50% off. Whether you want to try out a new skin care routine, stick to your exercise goals or cook some healthy new recipes for the new you in the new year, Amazon has you covered with some amazing deals. Shop this article: Amazon eero Pro 6 mesh Wi-Fi 6 system, Keurig K-Classic Coffee Maker, American Soft Linen Luxury 6 Piece Towel Set Get up to 50% off these bestsellers during Amazon’s New Year’s saleGive your skin a new year’s refresh with this Vitamin C serum from TruSkin. It has brightening properties that will help make your skin tone more even while lightening dark spots and smoothing out fine lines and wrinkles. During the New Year’s sale, it’s 56% off. The Original Peloton is 21% off during Amazon’s New Year’s sale, so you can start your New Year’s exercise goals off on the right foot. This indoor stationary bike is small-space friendly with its 4-by-2-foot footprint and features an immersive video screen where you can join workouts and compete with other Peloton owners. Amazon eero Pro 6 Mesh Wi-Fi 6 System The eero Pro 6 covers up to 6,000 square feet with mesh wifi technology that supports speeds up to a gigabit, so you can stream, game, work and more. It also doubles as a Zigbee smart home hub that can connect and control smart devices with Alexa. Get it during the New Year’s sale for 40% off. Lodge 10.25 Inch Cast Iron Pre-Seasoned Skillet This 10.25-inch skillet is pre-seasoned and ready to cook with. It can go from the stovetop to the oven, the grill and even a campfire, making it super versatile for all your cooking needs. Get it during the New Year’s sale for 42% off. The Keurig K-Classic Coffee Maker brews single-serve cups in two sizes. It’s programmable to auto-brew at set times and automatically turn off after idling to help save energy. Get it during the New Year’s sale for 47% off. American Soft Linen Luxury 6-Piece Towel Set This six-piece towel set includes two bath towels, two hand towels and two washcloths, available in 20 colors. Get it for 58% off during Amazon’s New Year’s sale. Fitbit Inspire 2 Health & Fitness Tracker Fitbit’s Inspire 2 Tracker features step, distance, activity, calorie and heart rate tracking and comes with a free one-year Fitbit Premium trial. Get it during the New Year’s sale for 23% off. The Apple Watch SE is 20% off during Amazon’s New Year’s sale, so you can get all the features that help you stay active, productive and connected. This model features fitness and sleep tracking, crash detection, a heart monitor, a Starlight aluminum case and more. HENCKELS Premium Quality 15-Piece Knife Set with Block This 15-piece knife set includes everything you need to outfit your kitchen: a 3-inch paring knife, 5-inch serrated utility knife, 7-inch santoku knife hollow edge, 8-inch chef’s knife, 8-inch bread knife, 4.5-inch steak knife set of 6, professional honing steel, kitchen shears and a hardwood knife block. Beats Solo3 Wireless On-Ear Headphones Get up to 40 hours of immersive listening time with Beats Solo3 Wireless On-Ear Headphones. They feature Apple’s W1 chip and Class 1 wireless Bluetooth connectivity for compatibility with both Apple and Android devices, plus adjustable fit and cushioned ear cups for comfortable, everyday use. Want to shop the best products at the best prices? Check out Daily Deals from BestReviews. Sign up here to receive the BestReviews weekly newsletter for useful advice on new products and noteworthy deals. Christina Marfice writes for BestReviews. BestReviews has helped millions of consumers simplify their purchasing decisions, saving them time and money. Copyright 2024 BestReviews, a Nexstar company. All rights reserved.  David Ryder As a dividend growth investor, the common belief is that companies not paying dividends don't fit into a portfolio centered on dividend growth. I beg to differ. Numerous outstanding companies exist that currently don't pay dividends and may not in the foreseeable future. Despite this, I choose to include the best of them in my portfolio due to their exceptional quality and substantial growth potential. Ultimately, the dividend yield reflects an average of all holdings in one's portfolio. Take Amazon.com Inc. (NASDAQ:AMZN) as a prime example — synonymous with quality and a 'must-have' for investors seeking growth. Consider this scenario: if you had invested $10,000 in 2010 and reinvested all the dividends into Amazon, S&P 500 (SPY), and Nasdaq 100 (QQQ), your returns would be as follows:
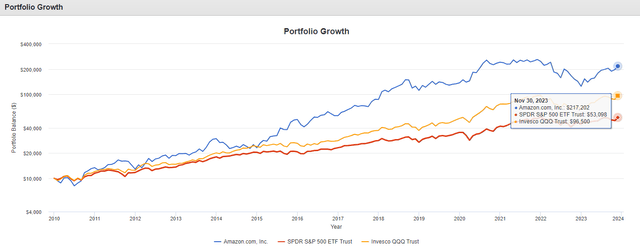
$10,000 Growth Since 2010 (Portfolio Visualizer) Having followed Amazon for more than a decade and holding it in my portfolio since 2015, I am writing my initial coverage of the company, assigning it an outperform rating heading into 2024. I view Amazon as being currently undervalued in light of its growth potential, and with the rate cuts coming in 2024, expect valuation expansion and significant growth ahead fueled by demand in its retail business and by AI tailwinds in Amazon Web Services or "AWS". 83% Gain Year-To-Date Without A Slow-Down In SightAmazon's stock surged during the pandemic as the demand for e-commerce soared. However, as the Fed began raising rates and economic worries surfaced in 2022, the shares plummeted by 49%. This year tells a very different story. Amazon's shares have skyrocketed by 83% year-to-date, marking its best performance since 2015, as well as overtaking FedEx (FDX) and UPS (UPS) as the US's No. 1 delivery business. Its market cap is now nearing $1.6 trillion, making it the fourth-largest stock in the S&P 500, trailing right behind Google's (GOOGL) A and B shares. You might be curious about expecting another stellar year for Amazon after its 2023 success. Yet, Amazon plans to leverage this year's gains by solidifying its leadership position and capitalizing on generative AI. It aims to enhance the profitability of its colossal online retail operations while setting the stage for continued growth. Amazon's Q3 2023 results showcase their remarkable success across various fronts and confirm the positive momentum. In the retail sector, the cost-to-serve, and delivery speed took significant strides forward, while AWS saw stabilized growth and advertising revenue experienced robust expansion. Overall, operating income and free cash flow saw notable increases. The Q3 net sales reached $143.1 billion, marking a 13% increase from Q3 2022's $127.1 billion. Adjusted for a $1.4 billion favorable impact from changes in foreign exchange rates, net sales grew by 11% compared to the same period last year. Operating income surged, surpassing fourfold to $11.2 billion in Q3 2023 from $2.5 billion in Q3 2022, driven by strong performances in both the retail and AWS sectors. This successful quarter translated to an increase in net income, reaching $9.9 billion in Q3 2023, or $0.94 per diluted share, compared to $2.9 billion, or $0.28 per diluted share, in Q3 2022. 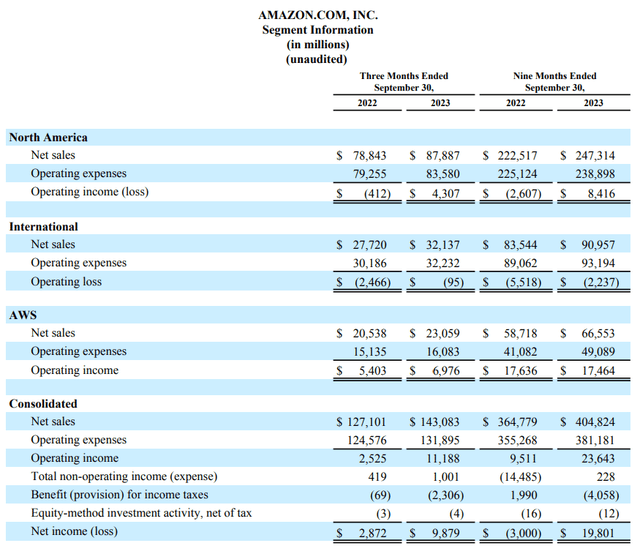
Financial Statement (AMZN IR) Operating cash flow witnessed a staggering 81% increase, totaling $71.7 billion for the trailing twelve months ending September 30, 2023, compared to $39.7 billion for the same period in 2022. Amazon is firing on all cylinders, witnessing growth and remarkable operational efficiency across all its businesses. Looking ahead, the spotlight for the upcoming year will focus on AI's integration into AWS. Recently, Amazon revealed a suite of new AI-centric products tailored for its expansive cloud computing division, AWS. During its annual re:Invent conference in late November, AWS leaders introduced a new chatbot for businesses, a deeper collaboration with Nvidia (NVDA), a frontrunner in AI chip technology, and an updated version of its own AI chip. These product launches underline Amazon's commitment to maintaining its dominance in the cloud services provider arena. As of Q2 2023, Amazon held a 32% market share, with Microsoft's Azure (MSFT) following at 22% and Google's Cloud at 11%. Analysts expect AWS to continue growing as more companies embrace compute-intensive generative AI products, capitalizing on its already substantial size and market share.  Cloud Market Share (Statista) The 2024 AI-focused narrative surrounding AWS brings up a recurring point often discussed here on Seeking Alpha: when you invest in Amazon's stock, you're essentially investing heavily in the AWS Business, while acquiring the Retail and Advertising Business at a discount. I agree with this statement to some extent, and here's why: During Q3 2023, AWS generated $6.976 billion in Operating Income, standing out as Amazon's most lucrative business, accounting for over 62% of the total $11.188 billion operating income in the quarter. While reaching the net income involves further deductions for non-operating income impacts and taxes, a rough estimate suggests that AWS contributed around $0.58 or 62% to the $0.94 diluted EPS for the quarter. Assuming a similar performance for the next three quarters, they could project an AWS EPS of $2.32 for FY24. For Retail and Advertising businesses, an anticipated EPS of $1.41 over the next four quarters seems reasonable, summing up to a total FY24 EPS of $3.73. Despite analysts forecasting an EPS of $3.49 in FY24, I hold the view that Amazon might surpass this estimate slightly. This belief rests on the foundation of AI advancements driving growth and a robust growth anticipated in both AWS and retail businesses, bolstered by the Fed's rate cuts. 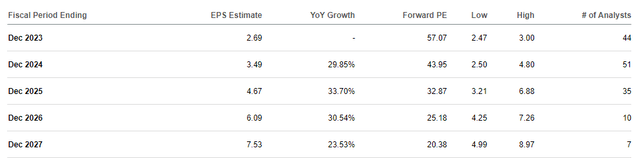
EPS Projections (Seeking Alpha) The current stock price stands at $153, and based on an anticipated FY24 EPS of $3.73, the Forward PE ratio rests at 41x, notably below its historical norms. With an expected EPS growth of 38.6% from FY23 to FY24 and no indication of growth slowing down due to improved operational efficiency, I propose that the stock should ideally be valued at around 60x its forward earnings. Should the valuation indeed expand to 60x its FY24 earnings of $3.73, my projected price target would be $224 by the end of 2024. This estimation suggests a potential stock appreciation of 46% from today's price.
As anticipated, the EPS growth is projected to persist in the coming years. Analyst estimates spanning from 2025 to 2028 suggest an average EPS growth of approximately 25.5%. However, considering a slight decline in this growth trajectory, I foresee a contraction in valuation towards 45x its forward earnings by 2028. This adjustment would potentially lead to a stock price of $416. While my scenario leans toward heavy bullishness, it's important to acknowledge the various risks that could potentially impede valuation expansion. Nevertheless, I firmly believe Amazon is presently trading at a discounted rate compared to its historical valuation. This assumption hinges on the expectation of robust EPS growth and the company's transition into a new phase of its life cycle characterized by significant improvements in operational efficiency, driving the bottom line of the business. To put it into perspective, Amazon has earned a place on multiple lucrative top-pick lists for 2024 curated by Wall Street:
Risks To My Bullish ThesisAt the moment, Amazon is gearing up for what could potentially be the most significant legal battle in its three-decade history. Regulators are questioning the company's market dominance, signaling that Amazon might face substantial scrutiny in the years ahead. The FTC alleges that the company has leveraged its market authority to inflate prices and overcharge merchants. In an October 3 client note, JPMorgan expressed that the lawsuit "was largely anticipated, and anticipates difficulties in proving that AMZN unlawfully sustains monopoly power." Simultaneously, the risk of an economic slowdown could act as a brake on Amazon's growth, impacting both its retail and AWS businesses. This risk remains, even if the Fed successfully engineers a soft landing in 2024, yet the GDP contracts more than expected. TakeawayAfter a challenging 2022, Amazon has bounced back, surging by 83% year-to-date. This upswing isn't driven by FOMO or market hysteria. Instead, the business is firing on all cylinders, witnessing recovery and growth across AWS, Retail, and Advertising sectors. I anticipate Amazon will capitalize on this momentum, marking 2024 as the onset of a new era focused on operational efficiency, paving the way for significant profitability. Presently, the valuation falls below historical averages. With expected rate cuts in 2024, I foresee valuation expansion, leading me to a bullish price target of $220 by the end of 2024, with further growth potential ahead. While I find the valuation of many businesses appealing, Amazon holds a spot among my top 5 picks for 2024. I anticipate a substantial rally and significant stock appreciation for the company. | ||||||||||||||||||||||||||||||||||||||||||
SCS-C01 study help | SCS-C01 test contents | SCS-C01 teaching | SCS-C01 education | SCS-C01 download | SCS-C01 test success | SCS-C01 syllabus | SCS-C01 book | SCS-C01 study tips | SCS-C01 testing | | ||||||||||||||||||||||||||||||||||||||||||
Killexams test Simulator Killexams Questions and Answers Killexams Exams List Search Exams |
SCS-C01 Reviews by Customers
Customer Reviews help to evaluate the exam performance in real test. Here all the reviews, reputation, success stories and ripoff reports provided.
100% Valid and Up to Date SCS-C01 Exam Questions
We hereby announce with the collaboration of world's leader in Certification Exam Dumps and Real Exam Questions with Practice Tests that, we offer Real Exam Questions of thousands of Certification Exams Free PDF with up to date VCE exam simulator Software.























