Real Exam Questions and Answers as experienced in Test Center
300-610 Braindumps with 100% Guaranteed Actual Questions | https:alphernet.com.au
300-610 course outline - Designing Cisco Data Center Infrastructure (DCID) Updated: 2024 | ||||||||||||||||
| Searching for 300-610 test dumps that works in real exam? | ||||||||||||||||
 |
||||||||||||||||
|
||||||||||||||||
|
Exam Code: 300-610 Designing Cisco Data Center Infrastructure (DCID) course outline January 2024 by Killexams.com team | ||||||||||||||||
300-610 Designing Cisco Data Center Infrastructure (DCID) DCID 300-610 Certifications: CCNP Data Center, Cisco Certified Specialist - Data Center Design Duration: 90 minutes Exam Description The Designing Cisco Data Center Infrastructure v1.0 (DCID 300-610) test is a 90-minute test associated with the CCNP Data Center and Cisco Certified Specialist - Data Center Design certifications. This test certifies a candidate's knowledge of data center infrastructure design including network, compute, storage network, and automation. The course, Designing Cisco Data Center Infrastructure, helps candidates to prepare for this exam. 35% 1.0 Network Design 1.1 Evaluate options for Layer 2 connectivity 1.1.a Endpoint mobility 1.1.b Redundancy/high availability 1.1.c Convergence 1.1.d Services insertion 1.2 Evaluate options for Layer 3 connectivity 1.2.a IP mobility 1.2.b Redundancy / high availability (graceful restart, NSF) 1.2.c Convergence 1.2.d Services insertion (load balancing, security) 1.3 Evaluate data center technologies such as vPC/vPC+ 1.4 Evaluate options for interconnecting data centers such as VXLAN EVPN and OTV 1.5 Evaluate options for device and routing virtualization 1.5.a VDC 1.5.b VRF (standard, VXLAN EVPN tenant) 1.6 Evaluate in-band and out-of-band options for management 1.7 Evaluate redundancy options such as active/active and disaster recovery site 25% 2.0 Compute Design 2.1 Evaluate options for Ethernet connectivity 2.1.a Redundancy / high availability 2.1.b Bandwidth (oversubscription) 2.1.c Fabric interconnect operation mode (switch mode, end host mode) 2.2 Evaluate options for storage connectivity 2.2.a Bandwidth (port-channels, oversubscription) 2.2.b Fabric interconnect operation mode (switch mode, end host mode) 2.2.c Direct-attached storage (appliance, FC storage, and FCoE ports) 2.3 Evaluate options for network device virtualization in a data center (Cisco VIC adapters) 2.3.a Number of interfaces vs. IOM uplinks 2.3.b vCon placement policies 2.3.c Ethernet adaptor policies 2.3.d Fibre Channel adapter policies 2.4 Evaluate options for hyperconverged infrastructure 2.4.a Cluster mode 2.4.b HX for virtual server 2.4.c Desktop virtualization 20% 3.0 Storage Network Design 3.1 Plan for iSCSI deployment in a data center (Multipathing and addressing schemes) 3.2 Evaluate QoS requirements in a data center 3.2.a Fibre Channel 3.2.b FCoE 3.2.c FCIP 3.2.d iSCSI 3.3 Determine FCoE/ Fibre Channel interface 3.3.a Dedicated and shared mode 3.3.b Port types 3.3.c ISL 3.3.d Oversubscription 3.4 Evaluate SAN topology options 20% 4.0 Automation Design 4.1 Evaluate options for network orchestration and automation 4.1.a DCNM 4.1.b Intersight 4.1.c NX-API 4.1.d Model-driven programmability 4.1.e Ansible 4.1.f Puppet 4.1.g Python 4.2 Evaluate options for compute orchestration and automation 4.2.a Service profile templates 4.2.b vNIC templates 4.2.c vHBA templates 4.2.d Global policies vs. local policies | ||||||||||||||||
| Designing Cisco Data Center Infrastructure (DCID) Cisco Infrastructure course outline | ||||||||||||||||
Other Cisco exams010-151 Cisco Certified Technician (CCT) for Data Center500-275 Securing Cisco Networks with Sourcefire FireAMP Endpoints CICSP Cisco IronPort Certified Security Professional 600-455 Deploying Cisco Unified Contact Center Enterprise (DUCCE) 500-210 SP Optical Technology Field Engineer Representative 500-052 Deploying Cisco Unified Contact Center Express (UCCXD) 500-651 Security Architecture for Systems Engineer (SASE) 500-701 Cisco Video Infrastructure Design (VID) 500-301 Cisco Cloud Collaboration Solutions 500-551 Cisco Networking: On-Premise and Cloud Solutions 700-020 Cisco Video Sales Essentials 500-710 Cisco Video Infrastructure Implementation 700-105 Cisco Midsize Collaboration Solutions for Account Managers 500-325 Cisco Collaboration Servers and Appliances 500-490 Designing Cisco Enterprise Networks 500-470 Cisco Enterprise Networks SDA, SDWAN and ISE test for System Engineers 500-901 Cisco Data Center Unified Computing Infrastructure Design 500-230 Cisco Service Provider Routing Field Engineer 700-150 Introduction to Cisco Sales 700-651 Cisco Collaboration Architecture Sales Essentials 700-751 Cisco SMB Product and Positioning Technical Overview (SMBSE) 300-410 Implementing Cisco Enterprise Advanced Routing and Services (ENARSI) 300-415 Implementing Cisco SD-WAN Solutions (ENSDWI) 300-420 Designing Cisco Enterprise Networks (ENSLD) 300-425 Designing Cisco Enterprise Wireless Networks (ENWLSD) 300-430 Implementing Cisco Enterprise Wireless Networks (ENWLSI) 2023 300-435 Automating Cisco Enterprise Solutions (ENAUTO) 300-510 Implementing Cisco Service Provider Advanced Routing Solutions (SPRI) 300-610 Designing Cisco Data Center Infrastructure (DCID) 300-615 Troubleshooting Cisco Data Center Infrastructure (DCIT) 300-620 Implementing Cisco Application Centric Infrastructure (DCACI) 300-635 Automating Cisco Data Center Solutions (DCAUTO) 300-810 Implementing Cisco Collaboration Applications (CLICA) 300-815 Implementing Cisco Advanced Call Control and Mobility Services (CLACCM) - CCNP 300-910 Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS) 300-920 Developing Applications for Cisco Webex and Webex Devices (DEVWBX) 350-401 Implementing Cisco Enterprise Network Core Technologies (ENCOR) 350-501 Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR) 350-601 Implementing Cisco Data Center Core Technologies (DCCOR) 350-701 Implementing and Operating Cisco Security Core Technologies (SCOR) 350-801 Implementing Cisco Collaboration Core Technologies (CLCOR) 350-901 Developing Applications using Cisco Core Platforms and APIs (DEVCOR) 500-215 SP Mobility Technology Systems Engineer Representative 200-301 Cisco Certified Network Associate - CCNA 2023 100-490 Cisco Certified Technician Routing & Switching (RSTECH) 200-201 Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) 200-901 DevNet Associate (DEVASC) 300-535 Automating Cisco Service Provider Solutions (SPAUTO) 300-710 Securing Networks with Cisco Firepower 300-715 Implementing and Configuring Cisco Identity Services Engine 300-720 Securing Email with Cisco Email Security Appliance 300-725 Securing the Web with Cisco Web Security Appliance (SWSA) 300-730 Implementing Secure Solutions with Virtual Private Networks 300-735 Automating Cisco Security Solutions (SAUTO) 300-820 Implementing Cisco Collaboration Cloud and Edge Solutions 300-835 Automating Cisco Collaboration Solutions (CLAUTO) 500-440 Designing Cisco Unified Contact Center Enterprise (UCCED) 600-660 Implementing Cisco Application Centric Infrastructure - Advanced 300-515 Implementing Cisco Service Provider VPN Services (SPVI) 300-915 Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT) 300-215 Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) 350-201 Performing CyberOps Using Core Security Technologies (CBRCOR) 500-240 Cisco Mobile Backhaul for Field Engineers (CMBFE) 700-765 Cisco Security Architecture for System Engineers 820-605 Cisco Customer Success Manager (CSM) 700-805 Cisco Renewals Manager (CRM) 500-452 Cisco Enterprise Networks Core and WAN (ENCWE) 700-760 Cisco Security Architecture for Account Managers 700-680 Cisco Collaboration SaaS Authorization (CSaaS) 700-846 Cisco IoT Advantage for Account Managers (IOTAAM)? 500-451 Cisco Enterprise Networks Unified Access test (ENUAE) 500-920 Cisco Data Center Unified Computing Infrastructure Troubleshooting (DCITUC) 500-220 Cisco Meraki Solutions Specialist (ECMS) 500-560 Cisco Networking: On-Premise and Cloud Solutions 500-445 Cisco Contact Center Enterprise Chat and Email (CCECE) 500-442 Administering Cisco Contact Center Enterprise (CCEA) 500-265 Cisco Advanced Security Architecture System Engineer (ASASE) 700-755 Small Business Technical Overview (SBTO) 500-444 Cisco Contact Center Enterprise Implementation and Troubleshooting (CCEIT) 500-443 Advanced Administration and Reporting of Contact Center Enterprise (CCEAAR) | ||||||||||||||||
| Our 300-610 dumps questions go through tough test of their certified experts. They review all the technical issues of 300-610 Questions and Answers before they are posted on their website for candidates to download. They keep their 300-610 dumps updating with real test questions and answers. Our vce test simulator is updated with latest changes in 300-610 braindumps. You can rely their 300-610 dumps for your real 300-610 test. | ||||||||||||||||
| 300-610 Dumps 300-610 Braindumps 300-610 Real Questions 300-610 Practice Test 300-610 dumps free Cisco 300-610 Designing Cisco Data Center Infrastructure (DCID) http://killexams.com/pass4sure/exam-detail/300-610 QUESTION 54 Which two configurations are available by using a service profile template in Cisco UCS Manager? (Choose two.) A. number of vHBAs B. ARP entries C. UUID assignment D. VXLAN membership E. target server Answer: AC Section: Automation Design Reference: https://www.cisco.com/c/en/us/td/docs/unified_computing/ucs/sw/cli/config/guide/2-2/b_UCSM_CLI_Configuration_Guide_2_2/b_UCSM_CLI_Configuration_Guide_2_2_chapter_0100000.html QUESTION 55 Which two types of service profile templates does Cisco UCS support? (Choose two.) A. initial B. permanent C. updating D. temporary E. connected Answer: AC Section: Automation Design Reference: https://www.cisco.com/en/US/docs/unified_computing/ucs/sw/gui/config/guide/141/UCSM_GUI_Configuration_Guide_141_chapter28.html#concept_C9D27CE2AA1245EA976DAA79F5BC6808 QUESTION 56 Which pools are used when a vNIC template is created in Cisco UCS Manager? A. WWPN B. UUID C. MAC D. IP Answer: C Section: Automation Design Reference: https://www.cisco.com/c/en/us/td/docs/unified_computing/ucs/ucs-manager/GUI-User-Guides/Network-Mgmt/3-1/b_UCSM_Network_Mgmt_Guide_3_1/b_UCSM_Network_Mgmt_Guide_3_1_chapter_0111.html QUESTION 57 Refer to the exhibit. Which template is used when a vHBA template pair is created for a specific server that inherits its attributes from an existing template? A. Secondary B. Initial C. Updating D. Primary Answer: B Section: Automation Design QUESTION 58 Which address pool is used when a vHBA template is created? A. MAC B. WWPN C. IP D. UUID Answer: B Section: Automation Design Reference: https://www.cisco.com/c/en/us/td/docs/unified_computing/ucs/sw/gui/config/guide/2-1/b_UCSM_GUI_Configuration_Guide_2_1/b_UCSM_GUI_Configuration_Guide_2_1_chapter_011010.html QUESTION 59 What are two functions of a Network Services Orchestrator in an NFV environment? (Choose two.) A. It operates at the resource-facing services layer and provides overall lifecycle management at the network service level. B. It provides an API-based northbound interface for transparent integration with systems that operate at the resource-facing services layer. C. It provides a standards-based southbound interface for transparent integration with systems that operate at the customer-facing services layer. D. It provides a standards-based northbound interface for transparent integration with systems that operate at the customer-facing services layer. E. It operates at the customer-facing services layer and provides the management interface for the virtual network devices. Answer: AB Section: Automation Design Reference: https://www.cisco.com/c/en/us/td/docs/net_mgmt/msx/3_4/solution_overview/Cisco_VMS_Sol_Overview.pdf QUESTION 60 Which feature provides a sandbox to convert NX-OS CLI commands to REST-based scripts on Cisco Nexus 7700 Series Switches? A. NX-API B. Postman C. Bash shell D. Guest shell Answer: A Section: Automation Design Reference: https://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus9000/sw/7-x/programmability/guide/b_Cisco_Nexus_9000_Series_NX-OS_Programmability_Guide_7x/b_Cisco_Nexus_9000_Series_NX- OS_Programmability_Guide_7x_chapter_010010.html For More exams visit https://killexams.com/vendors-exam-list Kill your test at First Attempt....Guaranteed! | ||||||||||||||||
|
The modern world thrives on the internet, even if there are some bizarre unintended consequences from tying everything to an Ethernet cable or wireless signal. And as networks grow, the demand for people who know how to design, build, maintain, and protect them becomes even more important. The 2021 Cisco CCNA & CCNP Certification Training Bundle will get you the certifications you need to become a professional network engineer. Both certifications were created by the networking company Cisco as they realized their products were becoming more complex, while educational materials weren't keeping up. For IT professionals, that's meant getting two key certifications, starting with the Cisco Certified Network Associate certification, or CCNA. Tied to the #200-301 exam, a CCNA certifies that you're able to set up, run, and maintain a network for a small or medium-sized business. The first course in this bundle explores that in detail with 150 lectures across nearly 47 hours discussing routing protocols, WAN technology, device monitoring and management and security fundamentals. Whether you're new to IT or just want to update your skills, it's perfect for all levels. Then the bundle turns to the Cisco Certified Network Professional certification, or CCNP. This expands on what you learned in the CCNA course to apply it to much larger networks, adding network architecture lessons, how to employ virtualization for users, and network infrastructure and assurance. Even if you're not going for your CCNP, it's information worth knowing for any IT professional or engineer who will deals with networks. Courses are run by ITU Online Training, which has won a ton of industry awards, including honors at the Best in Biz Awards and the Cybersecurity Excellence Awards. The demand for IT networking professionals is only growing, and a certification will help you move forward in your career, or launch a new one. The 2021 Cisco CCNA & CCNP Certification Training Bundle is normally $198, yet right now you can save 74% and get both courses for just $49.99. Prices subject to change. Futurism fans: To create this content, a non-editorial team worked with an affiliate partner. They may collect a small commission on items purchased through this page. This post does not necessarily reflect the views or the endorsement of the Futurism.com editorial staff. The Course Outline List component allows you to display a list of course outlines from the central Course Outlines Repository. The list can be filtered by term, course level, section and more to only show specific outlines. Note: If a course outline is not available at www.sfu.ca/outlines, it will not appear in the Course Outline List component. When should it be used?Use this component when you need to display multiple related course outlines on a single page. Be aware that the course outline list can get very long, depending on the filters. Terminology:Current - Two options, Year and Term, can be set to current, which refers to the current registration term. The current registration term will automatically rollover to the next term approximately 10 weeks prior to its start. In-Component Editing OptionsCourse Outline List Tab
Title Header - Insert a title above the course outline list. (If you wish to insert a title with a different size or style of heading, use a Text component.) Year - Filters outlines by year. If left blank, it will use the current year. Term - Filters outlines by term. If left blank, it will use the current registration term. Dept - Filter outlines by department. This is option is required. OptionsClick the Options toggle to reveal additional display options: Split list - Adds a header above each course. See example 2 for a preview. Show all sections - This option displays the outlines for all the sections, including tutorials and labs (e.g, D100, D115, D116, D118). Leaving this unchecked will display one outline for each parent section (e.g., D100, D200), regardless of how many child sections a parent may contain. This helps to reduce duplicate outlines. CSS Class - Allows an author to provide an optional class name that will apply a style to the contents. Filters Tab
Course Levels - Filter outlines by course level. Check each level you wish to display. If no levels are checked, the component will list all levels. Sections - Filter outlines by sections. By default, the component will list all sections. Columns Tab
Columns - Allows you to choose which columns to display. Please enable the “Note” column, if the “Short Note” field was filled in within the Course Outlines Application. Examples of the Course Outline Component
Example #1
This example was set up to show outlines for all 100-level Chemistry courses scheduled for Spring 2014. Earning specialized certifications is a surefire way to advance your career in the IT field, regardless of industry or current career level. The right certification validates your skills and knowledge, which makes you more desirable to future employers who want to attract and retain the best employees. Below, we’ll explore the top IT certifications and share how to examine your goals to choose the right path forward. We’ve narrowed IT certifications into specific categories to help IT professionals assess what’s available and pursue the best certifications to show their willingness to learn and develop the in-demand career skills employers want. Best database certificationsDatabase platforms have changed greatly over the years, but database technology remains important for various applications and computing tasks. Available certifications for IT professionals include those for database administrators (DBAs), database developers, data analysts and architects, business intelligence, and data warehousing specialists, and other data professionals. Obtaining database certifications demonstrates an understanding of database concepts, design, implementation, administration and security. This can boost your credibility in the job market and show potential employers that you have the skills needed to work with databases. The best database certifications include the following: Best SAS certificationsSAS is one of the world’s leading firms for business analytics, data warehousing and data mining. Today, the SAS Global Certification Program offers 23 credentials across categories including foundation tools, advanced analytics, business intelligence, data management and administration. SAS programmers remain in high demand, with a quick search of job boards showing thousands of open positions. Obtaining SAS certification shows employers that you are proficient in the company’s popular suite of tools. Some of SAS’s certification programs include the following: Many professionals earn certifications to help navigate their career paths. According to the IT Salary Report, 92 percent of information technology professionals have at least one certification. Best Cisco certificationsCisco Systems is a market leader not only in networking and communications products, but also storage networking and solutions for data centers. Cisco offers a variety of certifications for IT professionals, ranging from entry level credentials to expert-level exams. These certifications prepare professionals for Cisco-related careers. A search of job boards reveals thousands of open positions for Cisco experts, underscoring the continued relevance of these skills. Some of Cisco’s certifications include the following: Best Dell certificationsDell Technologies remains one of the world’s leading computing companies. In addition to its well-known hardware lineup, Dell also offers solutions for networks, storage, servers, gateways and embedded computing, as well as a broad range of IT and business services. Becoming certified in Dell products can help make IT professionals competitive in engineering roles for server, virtualization, networking, systems, integration and data security. Additional roles include consultants, account executives, system administrators, IT managers and deployment managers. Best mobility certificationsIn the mobile era, it has become increasingly important for network engineers to support local, remote and mobile users, as well as provide proper infrastructure. The focus on application and app development now leans more toward mobile environments, requiring security professionals to thoroughly address mobility from all perspectives. Due to the fast-changing nature of mobile technology, not many mobility certifications have become widely adopted. However, a few of the top mobility certifications can help IT professionals stand out in this rapidly evolving field. If part of your job includes selling and implementing an IT solution, you may want to pursue the best sales certifications. You’ll show your organization that you’re willing to go above and beyond to reach sales targets. Best computer hardware certificationsAs remote and computer-based work has become more common, it’s more important than ever that businesses and individuals be able to maintain their hardware. While discussions about potential computer-related jobs often revolve around software work and coding, jumping into the IT field by becoming a computer technician is an excellent starting point. Today, thousands of hardware technician jobs are available across the country. Entering this industry becomes more accessible for those who acquire computer hardware certifications. These certifications can showcase your expertise and proficiency in the upkeep of computers, mobile devices, printers and other hardware components. Best Google Cloud certificationsIT pros with solid cloud computing skills continue to be in high demand as more companies adopt cloud technologies. Today, Google Cloud is one of the market leaders in the cloud computing space. Regardless of where you are in your IT career, engaging with certification programs can demonstrate your willingness to keep on top of rapidly evolving cloud technologies. To that end, Google has introduced a host of certifications for its cloud platform, including the following: Best evergreen IT certificationsIn the fast-changing world of technology, it can help to focus on certifications that have stood the test of time. “Evergreen” refers to certifications that remain popular year after year. The top evergreen certifications are based on latest pay surveys in IT, reports from IT professionals about certifications they want or pursue the most, and those that appear most frequently in online job postings. Obtaining these credentials is one step toward ensuring that your skills remain relevant for a long time: Best IT governance certificationsIT governance provides structure for aligning a company’s IT with its business strategies. Organizations faced with compliance rigors always need experienced IT pros who can see the big picture and understand technology risks. This means certified IT governance professionals are likely to remain in high demand. Earning one of the following certifications proves a commitment to understanding the role of IT governance and its position in a company’s current and future success. Getting certified can validate your expert knowledge and lead to advanced career opportunities. Best system administrator certificationsAn IT system administrator is responsible for managing and maintaining the information technology infrastructure within an organization. The position demands sought-after career skills, ranging from configuring and maintaining servers and clients to managing access controls, network services, and addressing application resource requirements. If you’re in charge of managing modern servers, there’s a long list of tools and technologies that system administrators must master. Obtaining some of the most prominent system administrator certifications can demonstrate your mastery to potential employers. Best ITIL certificationsITIL, or Information Technology Infrastructure Library, was developed to establish standardized best practices for IT services within government agencies. Over the ensuing four decades, businesses of all types embraced, modified, and extended ITIL, shaping it into a comprehensive framework for managing IT service delivery. The ITIL framework remains the benchmark for best practices in IT service and delivery management, offering certification programs that cater to IT professionals at all levels. These training and certification courses ensure that IT professionals stay well-prepared for the ongoing evolution in IT service delivery management. There are four certifications in the ITIL certification program: Best enterprise architect certificationsAn IT enterprise architect is responsible for designing and managing the overall structure and framework of an organization’s information technology system. Enterprise architect certifications are among the highest that an IT professional can achieve; fewer than 1 percent ultimately reach this level. Enterprise architects are among the highest-paid employees and consultants in the tech industry. These certifications can put IT professionals on a path to many lucrative positions. The average worker earns over six figures annually. Some top enterprise architect certifications are listed below: To become an enterprise IT architect, you’ll need knowledge of systems deployment, design and architecture, as well as a strong business foundation. Best CompTIA certificationsCompTIA is a nonprofit trade association made up of more than 2,000 member organizations and 3,000 business partners. The organization’s vendor-neutral certification program is one of the best recognized in the IT industry. Since CompTIA developed its A+ credential in 1993, it has issued more than two million certifications. CompTIA certifications are grouped by skill set and focus on the real-world skills IT professionals need. Armed with these credentials, you can demonstrate that you know how to manage and support IT infrastructure. Best Oracle certificationsA longtime leader in database software, Oracle also offers cloud solutions, servers, engineered systems, storage, and more. The company has more than 430,000 customers in 175 countries. Today, Oracle’s training program offers six certification levels that span 16 product categories with more than 200 individual credentials. Considering the depth and breadth of this program — and the number of Oracle customers — it’s no surprise that Oracle certifications are highly sought after. Vendor-specific certifications address a particular vendor’s hardware and software. For example, you can pursue Oracle certifications and Dell certifications to become an expert in those companies’ environments. Best business continuity and disaster recovery certificationsBusiness continuity and disaster recovery keep systems running and data available in the event of interruptions or faults. These programs bring systems back to normal operation after a disaster has occurred. Business continuity and disaster recovery certifications are seeing a healthy uptrend as new cloud-based tools grow in popularity. While business continuity planning and disaster recovery planning have always been essential, they’re becoming more critical than ever — and IT certifications are following suit. Cisco on Wednesday unveiled a wide range of networking and storage switches, UCS equipment, and software aimed at unifying customers' entire data center infrastructures and helping prepare them for their step up into the cloud. Cisco also outlined several changes to its channel program the company said would make it easier for its solution provider partners to tie the new infrastructure products to complete solutions. The new hardware and software help cement Cisco's position as the premier provider of end-to-end data center infrastructure equipment, said Omar Sultan, senior manager for Cisco's data center architecture. "We're in a different position when compared to their competitors," Sultan said. "We have a full product portfolio with a broad vision and the ability to execute against that vision." One of the bases of that vision is Cisco's Unified Fabric, which refers to the company's ability to provide end-to-end network convergence, Sultan said. To help Strengthen that convergence, Cisco introduced two new series of Nexus data center switches along with enhanced connectivity and management capabilities across a wide range of its data center networking product line. The company unveiled the Nexus 5548UP 48-port and Nexus 5596UP 96-port data center switches with unified port capability. These two switches not only increase the port count over previous models, they also allow customers to configure every one of the ports for Gbit Ethernet, 10-Gbit Ethernet, Fibre Channel over Ethernet (FCOE), or 8-Gbit Fibre Channel, Sultan said. Cisco in the second half of 2011 plans to add its FabricPath technology to its Nexus 5000 switches. FabricPath is a scalable virtual networking technology that combines networking Layer 2 flexibility and Layer 3 scalability to allow virtual machine portability across an entire network. It is Cisco's subset of the proposed TRILL (Transparent Interconnect of Lots of Links) protocol, Sultan said. Also new are the Cisco Nexus 3000 Series switches which provide low latency of less than 1 microsecond from port-to-port in a high-density 10-Gbit Ethernet environment. The Nexus 3000 switches are designed for high-performance computing environments running high-speed financial and other applications, he said. For its Nexus 7000 Series switches, Cisco is adding the ability to support up to 1,500 Gbit Ethernet or 1,000 10-Gbit Ethernet ports. The company is also adding new Layer 3 VPN capabilities. The enhancements are scheduled to ship next quarter, Sultan said. Cisco introduced two new enhancements to its fabric extender technology (FEX). FEX technology is a series of 1U appliances which let a parent Nexus switch provide a scalable unified server-access platform across a range of Ethernet and blade server environments. The first enhancement, Adapter FEX, allows a single physical network interface card (NIC) to be split into multiple NICs, making it easier to utilize existing NICs to manage applications in virtualized environments. The second enhancement, VM-FEX, extends the switching fabric to connect directly to server hypervisors in virtualized environments in order to consolidate virtual and physical access layers into a single point of management, Sultan said. Cisco is also enhancing end-to-end network convergence from servers to storage with the addition of multi-hop FCoE capabilities to its Nexus 7000 and Nexus 5000 data center switches and its MDS 9500 storage switches. Multi-hop FCoE allows up to seven "hops" or connections between the storage host and target, compared to typical FCoE technology which provides only a single hop, Sultan said. "This allows you to move your convergence point closer to the SAN," he said. Next: Helping Prepare Data Centers For The Cloud To help prepare customers' data center infrastructures for cloud services, Cisco is preparing to implement the Locator/Identifier Separation Protocol (LISP). LISP breaks the connection between the identity of a user of a workload and that user's location, making it possible to move workloads regardless of where the user is located, Sultan said. For instance, in follow-the-Sun applications which move from data center to data center over the course of a day, LISP will allow a workload to move while maintaining the same IP address so that users can find it wherever it is, he said. LISP also enables workloads to move to and from the cloud without breaking the IP address, he said. For its Catalyst 6500 storage switches, Cisco is introducing several new modules including new ACE-30 for dynamic workload balancing, the ASA Service Module firewall appliance, and the ES-50 module with the DCI (Data Center Interconnect) interconnect to allow 40-Gbit bandwidth between two 6500s, Sultan said. On the server side, Cisco is upgrading its Cisco UCS (Unified Computing System), which combines networking, blade servers, storage, core switching, routing, security, and voice over IP (VoIP) into a single architecture. The company introduced a new blade server, the UCS C260 M2, which features two sockets for the Intel Westmere-EX processors, up to 1 TB of memory, and up to 16 SSDs or hard drives totaling up to 9.6 TBs of storage capacity. The UCS C260 M2 is targeted at OLTP (online transaction processing) and data warehousing applications, Sultan said. Cisco is also updating its UCS C460 M2, UCS B440 M2, and UCS B230 M2 servers with the Westmere-EX processors. For solution providers, Cisco is offering new promotions and enhancing its channel program to go with the new unified data center offerings, said Dave Gronner, senior manager of worldwide channels for data center technologies at Cisco. In the second half of 2011, Cisco plans to offer a new data center and cloud accelerator promotion which provides solution providers additional backend rebates on incremental deals, Gronner said. The company will also increase the backend rebate for incremental data center solutions sold into registered deals. Gronner declined to specify the amount of the additional rebates. Cisco also introduced a new remote data center and virtualization lab that allows channel partners to log in with customers to play with and demonstrate the new solutions, Gronner said. "Not every partner can restructure its own labs for a new demo," he said. "Partners can run their own labs. But we're giving them the benefit of a large environment which they don't need to run on their own." Cisco is also providing its partners with new tools to do data center assessments for customers. These tools, which go beyond those which Cisco has offered for years for network assessments, let solution providers to do an inventory analysis of data center equipment and identify potential issues related to latency, gaps, or CPUs, Gronner said. "These assessments are one of the most powerful ways for partners to identify issues and help customers solve them," he said. Finally, Cisco is introducing complete data center marketing campaigns that partners can use, Gronner said. These "campaigns-in-a-box" include all the collateral solution providers need to develop their campaigns, and within the next two months will encompass all the new products released unveiled on Wednesday, he said. Course Outlines and Syllabi
Course Outlines A one-page course outline is required by university policy for every course offered by the Faculty of Health Sciences. Instructors will receive an email reminder through TRACS to upload their course outlines. Outlines must be available to students at least two weeks prior to the start of the registration period or two months before the semester begins (March, July and November). Note that the one-page outline is different than the syllabus. See below for syllabus information. Instructors upload their course outlines online. Please follow these instructions:
Before your outline is activated online, the program assistant will review to ensure that all required fields are complete. If you have taught the course before, you may want to use the previous outline as a starting point and make any desired changes. The course content should correspond to the SFU Calendar description. If it does not conform closely, you must apply for approval before any changes can be published. Contact the appropriate program assistant, depending on whether you are teaching an undergraduate or graduate course, if you have not taught a course before and would like a copy of a previous course outline for your reference, or if you would like to apply for approval to upload content that does not closely conform to the SFU Calendar description. Refer to this link to search for the archived course outlines: http://www.sfu.ca/outlines.html. The system has archived outlines starting from Fall 2015 onwards. Course Syllabi and Syllabus Policies Refer to the Policies and Procedures Related to Syllabi Review, Development and Distribution (this link requires your ID to login) for more guidance about drafting a syllabi and to locate a syllabi template. All HSCI courses at both the graduate and undergraduate levels must have a detailed syllabus that delineates course objectives and means of assessment. Attached to this policy is a template to help you design of a syllabus so that it outlines the appropriate level of detail in terms of content, objectives, and assessment tools. The recommended text in regards to grading distributions, student conduct, and other policies are also provided. All new and substantively updated/revised courses must be reviewed as indicated below. Syllabi submitted for review do not need to be in the final draft. The GSC and UGSC are generally concerned with the review of the following: 1) the statement of learning objectives; 2) an outline of topics; and 3) a list of required readings/texts. You will receive an email from the TRACS system to upload your syllabus, in accordance with the following schedule:
For new or substantially revised courses, feedback will be provided to instructors three weeks prior to the start of the term. Notably for graduate courses, where accreditation requirements demand that courses meet certain core competency requirements, it is expected that faculty will comply with requests for revision. The course syllabus represents a contract between the instructor and student. It is important that it clearly outlines expectations, grading and attendance policies, and appropriate student conduct guidelines to all students enrolled in the course. A syllabus does not need to be provided in hard copy and can be distributed through Canvas or through other online formats. The scheduling of syllabus may be changed after the start of a term, but once the syllabus has been circulated to students, it is strongly advised not to make further changes to: a) grading policies; b) policies regarding student conduct and academic honesty; or c) the timing of key exams. For more resources and guidelines, refer to the links below:
Getting Into The Cloud Ring Cisco Systems and Hewlett-Packard are neck and neck in the rapidly growing cloud infrastructure equipment market, with both companies owning just over 13 percent of the worldwide market share by revenue, according to new data from Synergy Research Group. The networking giant has a clear lead in the public cloud infrastructure market, while HP is beating Cisco on the private cloud side. Synergy reports that total cloud infrastructure equipment revenues for the first quarter of the current fiscal year were more than $14.5 billion, representing a 25 percent year-over-year growth. CRN spoke with Jeremy Duke, founder and chief analyst at Synergy, and solution providers about how the two rivals are leading the market and who will ultimately win.
Cisco Riding A 6 Percent Lead In Public Cloud Cisco is leading the public cloud, with 15 percent of market share, followed by HP at 9 percent and Dell at 6 percent. "Cisco is tied in with VCE around the vBlock technology, and Cisco is tied in with NetApp around FlexPod. They offer quick turn-key solutions to getting these types of things going. Not that HP doesn't offer them, but that's what gives Cisco an advantage," said a top executive at one Northeast solution provider who partners with HP and Cisco. "Telecoms are typically the ones building the bigger public clouds, and HP doesn't really play like Cisco in that telecom market." The San Jose, Calif.-based networking giant's 6 percentage point market share lead over HP on the public side mainly stems from its already established share of the networking segment and its growing position in servers, according to Duke. " Cisco has come from the initial infrastructure build-out of what they have now come to know as the Internet," said Duke. "For Cisco, a significant disruptive decision was to invest in blade servers, which was then followed with Cisco building specialized algorithms and ASICs to make servers, networking and storage work together optimally."
HP No. 2 In Public Cloud Palo Alto, Calif.-based HP holds the No. 2 spot in the public cloud, with 9 percent. HP touts its Helion Public Cloud as a transparent, enterprise-grade public cloud based on OpenStack technology, offering pay-as-you-go cloud services for computing and storage infrastructure as well as platform services. "Helion has a great message, [but it's] not practical," said another executive solution provider on CRN's Solution Provider 500 list who partners with Cisco and HP. "I don't know of many true Helion deployments." HP created a scare in the partner community after The New York Times reported that the company would be "ceding" public cloud market. Although executives later denied the report, partners are also wondering if HP's splitting into two companies will have an impact on the enterprise market. "Since HP's No. 2 here, there's no need to panic, but I'm wondering what they're going to look like in this [space] in a year," said the SP500 executive. "We're all hoping the split-up goes through smoothly."
HP Winning Private Cloud By 5 Percent HP is in the No. 1 spot when it comes to the share of private cloud infrastructure, owning 16 percent of the market, followed by Microsoft with 13 percent share, then Cisco at 11 percent. The company's private cloud dominance is the result of its strong legacy as an enterprise server vendor, said Duke. "HP has been a strong foundational part of private enterprise and SMB IT infrastructure for decades, with HP's flagship data center and cloud offering being based around server computing," said Duke. "For organizations that are truly building their own private cloud internally -- they may be building on things like OpenStack or Linux KVM -- those types of technologies, the commodity hardware that HP has plays much better than the Cisco stuff from a cost perspective," said the Northeast solution provider executive.
Cisco Trails HP, Microsoft In Private Cloud Cisco sits at the No. 3 spot in the private cloud market, lagging behind HP by 5 percentage points. Partners said Cisco's Intercloud strategy of hybrid clouds isn't resonating quite yet with customers in 2015 as much as they anticipated, which could be impacting its private cloud sales. "[Cisco's] really pushing hybrid IT, instead of solely private cloud," said the Northeast solution provider. "HP had the Moonshot program that went out that had very dense servers for scalability, which might have taken some [share] from Cisco here." The networking giant in April did unveil a new OpenStack Private Cloud Bundle and new financing option aimed at enabling channel partners to sell its OpenStack Private Cloud offering, which it gained in September through its acquisition of Metacloud.
Total Cloud Market HP’s growth over the past four quarters has slightly outpaced Cisco's, allowing it to close the gap on its biggest competitor, according to Duke. The rival companies are racing side by side for the total cloud infrastructure equipment race -- both hovering at 13 percent, followed by Microsoft at 8 percent. "The fundamental reason for HP's and Cisco's current leading share position really comes down to where each vendor started from, in that their starting point has led and defined their path to where they are today," said Duke. "For the future, … this is where things are going to get very interesting."
Who's Going To Win? "If you look at it from the network and the converged infrastructure, I do think Cisco definitely has a leg up," said the Northeast solution provider executive. "HP to me, it's not that they don't have the solutions out there, I just don't see the sales and marketing as orchestrated quite as well as Cisco. I would hedge my bet on Cisco over HP." Duke says whichever advances the development of its computational, networking platforms and creates software that fully optimizes the infrastructure will win the market. Advances must come in the form of management and orchestration of networking and storage platforms such as OpenStack. Additionally, advances in enterprise collaboration platforms and automation are needed, says Duke. "I think the public cloud ranking is the only one that is real, since I know of very few true private clouds in the world," said the SP500 executive. "So I would go with Cisco."
Other Key Players Several other vendors have seen year-on-year cloud revenue growth rates in excess of 20 percent, says Duke, while original design manufacturers (ODMs) are also benefitting from hyperscale cloud providers' outsourcing the supply of their own designed hardware. For total cloud infrastructure, Microsoft was in third place at 8 percent, followed by Dell, IBM, and EMC, which are all in the 4 percent to 7 percent market share range. VMware and Lenovo both have 3 percent or less market share. Microsoft and VMware are key players in the total cloud ranking because of their positions in server operating system and virtualization applications, while IBM maintains a strong presence across a range of cloud markets. The Cisco Talos Year in Review report released Tuesday highlights new trends in the cybersecurity threat landscape. We’ll focus on three syllabus covered: the ransomware cybercriminal ecosystem, network infrastructure attacks and commodity loader malware. More ransomware actors switched to extortion rather than encryption, while commodity loaders evolved to be stealthier and highly effective, although new major security improvements have seen the day in 2023, such as Microsoft Office disabling macros by default. Network devices are increasingly impacted by cybercriminals and state-sponsored threat actors. Jump to: The ransomware cybercriminal ecosystem changedMost targeted verticalIn terms of ransomware, the most targeted vertical, as observed by Cisco Talos in 2023, was the healthcare and public health sector, which is not surprising since the organizations in that sector often suffer from underfunded budgets for cybersecurity and low downtime tolerance (Figure A). In addition, those organizations are interesting targets because they possess protected health information. Figure A 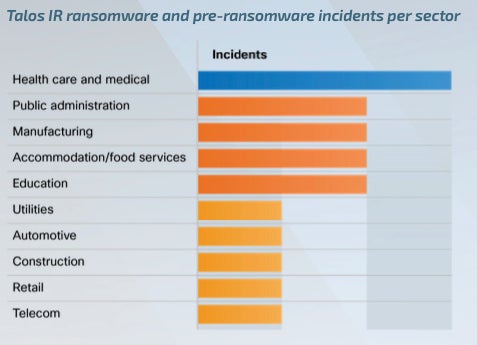
Some ransomware groups have been changingThe most active ransomware group for the second year in a row was LockBit (25.3% of the total number of posts made to data leak sites), followed by ALPHV (10.7%) and Clop (8.2%). Yet some ransomware groups kept changing in 2023; those structures often merged or rebranded in an attempt to confuse law enforcement and researchers tracking them. The cybercriminals active in the field often work for several ransomware-as-a-service services at the same time. Multiple leaks of ransomware source code and builders also affected the ransomware threat landscape because these allowed more people (even those with little technical knowledge) to start their own operations. Zero-days exploited at an unprecedented paceHighly technical actors have been exploiting zero-day vulnerabilities at an unprecedented pace. The Clop ransomware group in particular has been able to exploit multiple zero-day vulnerabilities, including vulnerabilities in the GoAnywhere MFT platform, MOVEit and PaperCut. Cisco Talos states that “Clop’s repeated efforts to exploit zero-day vulnerabilities is highly unusual for a ransomware group given the resources required to develop such capabilities,” yet it is still unsure that they do develop exploits on their own. When questioned about it in an email interview, a Cisco spokesperson told TechRepublic, “Because of the murkiness in the relationships that constitute the ransomware ecosystem, it can be difficult to accurately parse out which personnel/organizations are responsible for which actions. Because of this, they do not have direct insight into how Cl0p obtained the 0days and have not observed any indications that they purchased them. Regardless of whether they developed them themselves or purchased them, the usage suggests Cl0p is well-resourced, either in engineering talent or in finances and connections that would allow them to obtain from a third party.” More affiliates are using a data theft extortion modelAnother remarkable shift in the ransomware threat landscape is that more affiliates are now switching to a data theft extortion model rather than the usual encryption model. In these attacks, cybercriminals do not deploy ransomware; instead, they steal organizations’ sensitive information before asking for a ransom. The improvements in ransomware detection capabilities from Endpoint Detection and Response and Extended Detection and Response software might be one reason for switching tactics and stopping deploying ransomware on the targeted systems. Cisco Talos also suspects the aggressive pursuits from U.S. and international law enforcement against ransomware actors might be another reason for that change. Network infrastructure attacks increasedCisco Talos observed an increase in attacks on networking devices in 2023, particularly attacks operated by China- and Russia-based groups looking to advance espionage objectives and facilitate stealthy operations against secondary targets. The researchers observed such activity from other cybercriminals, including initial access brokers and ransomware threat actors. Weak security on network devicesNetworking devices, although being key components to any organization’s IT infrastructure, are not often examined from a security point of view and are often poorly patched, making them an interesting target for cybercriminals. Yet those devices often run on non-standard operating systems, rendering their exploitation harder by cybercriminals but also unmonitored by standard security solutions. The typical compromise of those devices starts with threat actors exploiting unpatched vulnerabilities, weak or default credentials, or insecure device configuration. A Cisco spokesman told TechRepublic that “the continued prevalence of default credentials may be partly explained by the sheer number of vendors and products combined with the lack of uniform standards/best practices. The move away from default credentials should certainly help Strengthen the situation. It is important to note that weak credentials can also be exploited if the actor is able to brute-force or password-spray, and that access brokers still achieve success in obtaining credentials and selling them on the dark web. This means that even if organizations are not using default credentials, it’s essential they create unique and complex passwords, employ MFA where possible, and emphasize additional security measures such as segmentation and IR planning as well.” Targeted devices had a high severity scoreVulnerabilities affecting network devices in 2023 all had a high severity score, meaning those devices were easily exploitable and had the potential to cause significant operational impact, according to Cisco Talos. Once compromised, those devices allow attackers to capture sensitive network information, facilitating further access to the target’s networks. Attackers also might plant malware on the devices to establish an initial foothold in the target’s infrastructure without the need for any authentication, or to redirect network traffic to actor-controlled servers. Finally, the devices are also often used by attackers as anonymization proxies for conducting attacks on other targets. Commodity loader malware evolvedCommodity loader malware such as Qakbot, Ursnif, Emotet, Trickbot and IcedID have been around for years. They were initially banking trojans, looking for credit card information theft on infected computers. In late 2023, new variants of IcedID and Ursnif appeared with a striking difference as compared to their older versions: Their banking trojan capabilities had been removed, and their dropper functionalities had been improved. The IcedID new samples have been used by initial access brokers known for commonly selling network accesses to ransomware groups. The latest Ursnif variants were used by the Royal ransomware group. Qakbot also evolved, deploying new features ideally suited to help ransomware groups. This evolution from banking trojan to loader is attractive for cybercriminals who want to be stealthier; the banking trojan function removal renders those malware less detectable. The infecting vector for Qakbot, IcedID and Ursnif evolved, as Microsoft’s new security measures on Office products affected the malware threat landscape, forcing cybercriminals to find new ways to use macros undetected or avoid using them completely (Figure B). Figure B 
Threat actors used different methods compared to previous years for spreading their malware and infecting devices, such as using JavaScript, PowerShell, OneNote documents, or HTA files, to name a few. They also used the Google Ads platform to deploy malware such as Ursnif, IcedID or Trickbot, fully avoiding macros. Some other threat actors deploying Emotet, IcedID and Ursnif have been observed using older methods with macros, probably because the success rate on unpatched enterprise legacy systems is still high. How to protect your business from these cybersecurity threatsThe threat landscape evolves to suit cybercriminals’ needs, and your security team needs to ensure its mitigation strategies are keeping up with the trends. Here are some tips for securing your business from these cyberthreats. In addition, all operating systems and software must be up to date and patched to avoid being compromised by common vulnerabilities. RansomwareAccess control mechanisms should be carefully reviewed in all corporate environments, and data segmentation should be applied for storing sensitive data because ransomware threat actors are increasingly trying to steal sensitive data rather than encrypt it. Network devicesNetwork devices must be up to date and patched. Default passwords, if any, must be changed to strong passwords. All of the devices’ configuration files should be carefully analyzed and tuned to avoid any malicious exploitation. When possible, multifactor authentication must be deployed on those devices. Also, inbound and outbound communications from the devices should be monitored to detect malicious communication. Commodity loadersThe main families of commodity loaders have dropped their banking trojan capabilities to be lighter and stealthier, even without using macros — often to facilitate ransomware operations. Organizations should educate their employees to handle more file types with caution, such as PDF files or ZIP archives that might contain malicious files. Disclosure: I work for Trend Micro, but the views expressed in this article are mine. Udemy’s Complete Cryptocurrency Investment Course covers all of the fundamentals of cryptocurrency investing in an affordable, self-paced, mobile-friendly format, making it the best overall cryptocurrency trading course on their list. Founded in 2009, Udemy has since grown to become one of the largest online learning platforms offering over 210,000 courses taught by more than 75,000 instructors in 75 languages. Its Complete Cryptocurrency Investment Course introduces students to the basics of cryptocurrencies and advances them quickly into investing techniques featuring live examples. As a result, it’s their clear choice as the best course overall. The Complete Cryptocurrency Investment Course is led by Mohsen Hassan, a programmer, trader, and financial risk manager who has taught investing to more than 300,000 Udemy students. The course consists of over 12.5 hours of on-demand video, one article, and two downloadable resources and can be accessed on the Udemy mobile app. The Complete Cryptocurrency Investment Course walks beginners through the fundamentals of cryptocurrency and quickly moves to live examples of buying, transferring, and using wallets as well as portfolio management techniques for both passive and active investing. Through this course, Hassan buys, transfers, secures, and builds a portfolio with real money so students can see exactly how it’s done. The Complete Cryptocurrency Investment Course costs just $99.99 and includes full lifetime access, a certificate of completion at the end of the course, and a 30-day money-back guarantee. Udemy runs specials all the time, so you may be able to purchase the course for a much lower price. | ||||||||||||||||
300-610 test plan | 300-610 study | 300-610 test contents | 300-610 PDF Download | 300-610 basics | 300-610 Questions and Answers | 300-610 Practice Test | 300-610 test | 300-610 test contents | 300-610 test Questions | | ||||||||||||||||
Killexams test Simulator Killexams Questions and Answers Killexams Exams List Search Exams |
300-610 Reviews by Customers
Customer Reviews help to evaluate the exam performance in real test. Here all the reviews, reputation, success stories and ripoff reports provided.
100% Valid and Up to Date 300-610 Exam Questions
We hereby announce with the collaboration of world's leader in Certification Exam Dumps and Real Exam Questions with Practice Tests that, we offer Real Exam Questions of thousands of Certification Exams Free PDF with up to date VCE exam simulator Software.